Okay, I have finally got an introduction. Let's begin with - what can you do with XMPP? How about join the best place on the Internet - Diggy's group chat at digdeeper@conference.jabber.lqdn.fr. There, you can make friends, call each other cucks, and discuss topics such as privacy, software, conspiracies, philosophy, and religion with exclusively 120+ IQ people :D. There are no rules in terms of content posted, no enforcing the "right opinions". Anyway, what makes XMPP superior to other protocols? It is old, time-tested, and has a lot of features. It is decentralized - anyone can run his own server or you can use any of the probably hundreds of servers available. Anonymous (TOR / VPN) and private (no personal data like real name or E-mail) sign-up is available from inside the clients - of which there are many, satisfying everyone. As far as I can see, no big malicious corpo has compromised XMPP - unlike Discord (lol) or Matrix. XMPP does not require a phone number like other common instant messengers - such as Signal or Telegram. Anyway, let me review the available XMPP clients:
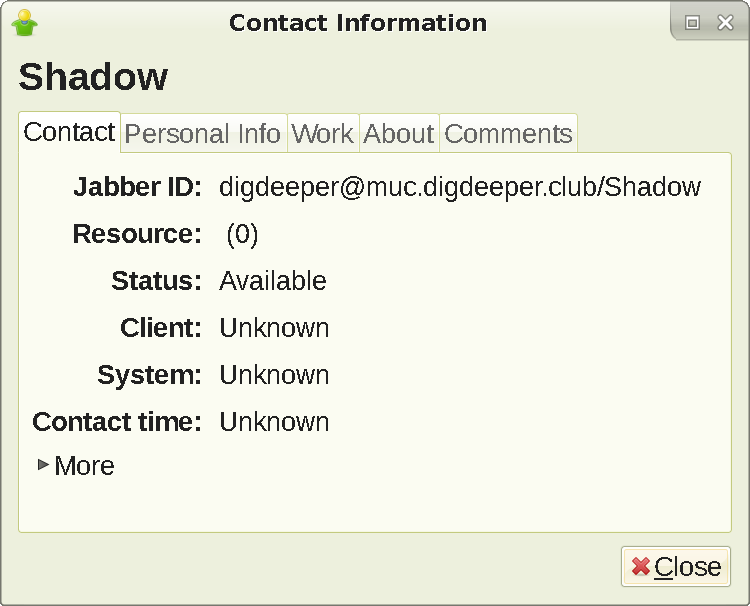
Psi+ has an extreme amount of options. This can get very confusing and most of those options appear to be unnecessary, but if you like tinkering, this is the client for you. Psi+, by default, reveals your timezone, client (version and creation date), and system information (full hostname). You can modify the resource header, but it doesn't do anything to remove the data leaks. The way to mitigate it is by using the plugin Client Switcher. Choose not implemented
as the Response mode
. Then, you need to Enable for
Contacts
and Groupchats
. Finally, mark Deny iq time request
. This will show Unknown for all categories when inspected. You can also falsify your client and system info - only Psi+ can do that. Psi+ supports OMEMO and OTR. Seems to show more previous messages in group chats than all other clients. Requires QT, and if you rely on GTK themes, will look ugly and inconsistent with the rest of the system. Version tested: 1.4.650, as that is what is available in SlackBuilds. Most distros don't package Psi+ at all, it seems - and if they do, the versions are old. Edit: someone has notified me that in version 1.5.1618.0 for Windows, the STUN server defaults to Google's - but this can be easily disabled. Anyway, here is an image showing how to falsify Psi+ info, and the results:

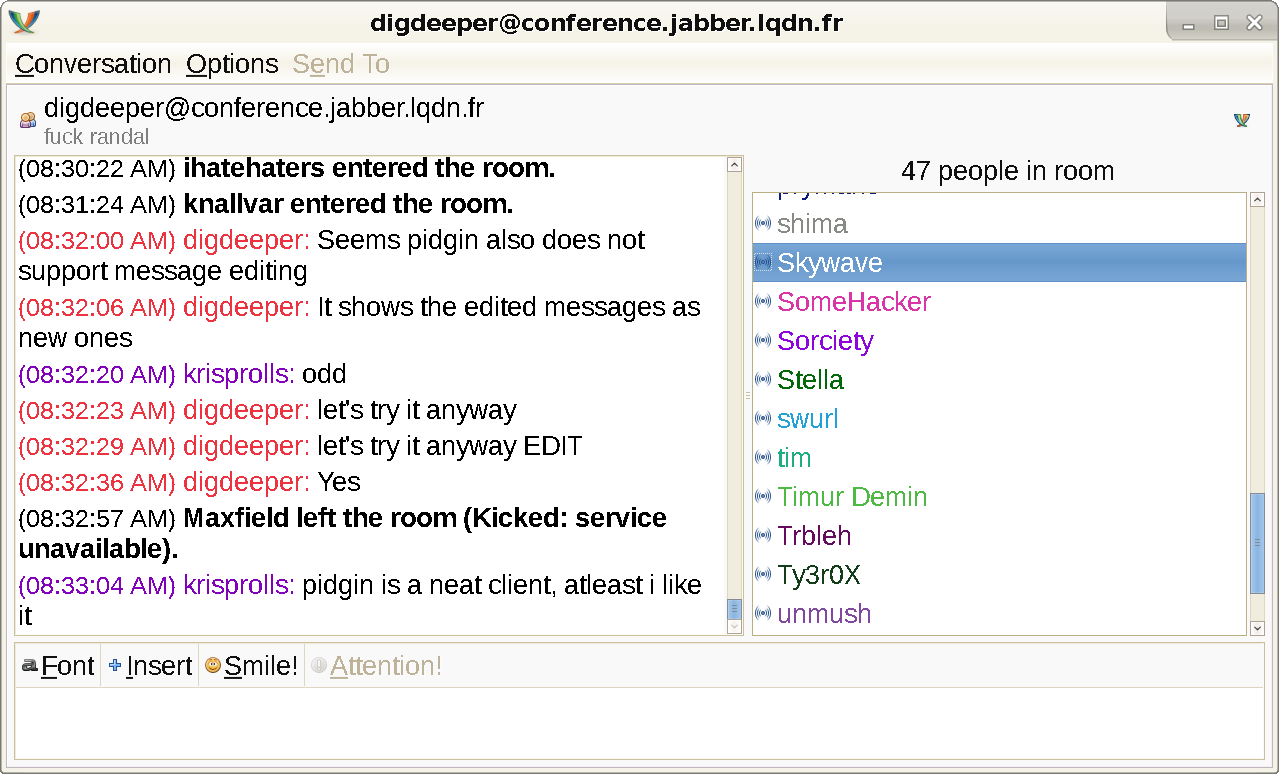
Doubles as a client for IRC and some other protocols. I really like the UI, which relies on GTK2. Leaks your client and version (for example, Pidgin 2.11.0 (libpurple 2.11.0)) and timezone, but not system info unlike Psi+ (it shows up as Unknown); these leaks also cannot be disabled. Supports OTR and OMEMO, but the OMEMO plugin is terminal-based and sucks (cannot accept or remove fingerprints). Decent program in terms of design, but due to the data leaks and bad OMEMO support, cannot be recommended. However, if you really want to use Pidgin, you can nullify the timezone leak by changing the system's timezone; this does not fully prevent it, just displays a fake value. This way will also affect other things in your system, like the clock. Edit: on Windows, RunAsDate can be used to spoof the timezone. Pidgin cannot connect to onion domains, failing with the SSL handshake failed
error - regardless of any settings. Yet another significant flaw, which means Gajim is superior unless you need the other prococols. Pidgin does not support message editing either, showing the modified messages as new ones:
Leaks client and version (for example, Conversations 2.10.2+fcr) plus timezone and the fact that it's on Android (but no specific system info). This applies to all the Conversations family. Using them through TOR prevents the timezone leak, but still leaks everything else. All Android XMPP clients auto-invite you to group chats, leading to easy trolling. There is no way to mitigate any phone client in full unless you use Diggy's black magic. Usability wise, compared to ChatSecure, It's a little clunky... Scrolling and menu changes jump around and switching between group and one on one chats is horrendous. I also have to go through two sub sections to change OMEMO settings to blindly accept or save or reject. With ChatSecure I could look at OMEMO keys in each chat. Conversations requires me to go out of chat to main settings and then a sub configuration menus. Just tedious. I don't get any indication on your status. ChatSecure had a green ring around each avatar when someone was online and how many hours ago.
For something more positive, ChatSecure never told me when someone left but Conversations actually did with a visual change too
.
Does not leak timezone, client version, or system information. Does leak its name in the resource header - this means that all clients expose it, instead of just Psi and Gajim. UPDATE May 2022: new version has multiple account support and MUC invitations, so it's not as useless now. Cannot connect to onions. GTK3 dependence. No OTR; does support OMEMO well though.
Terminal-based. Can disable leaked system info and timezone, but not the client and version. UPDATE: people have told me OMEMO does not work properly in it when talking with other clients such as Dino. UPDATE 2: I got told that it is hard to recognize you have been mentioned (quoted) when you have been away for a few hours.
My favorite client. Old versions use GTK2 and look great. Full support for OTR, PGP and OMEMO. Can fully disable all data leaks except client name, that can only be revealed by Psi+ and other Gajim. Unlike Dino, it has all the relevant features, but no bloat as in Psi+. Why use an old version? The new ones use GTK3, which is inconsistent with the rest of the system that uses GTK2 and has a much more complicated theme engine (makes it almost impossible to create your own theme if you want). New versions add nothing except a Discordized UI and the GTK3 dependency. There are no security issues in any version from 0.16.7 up until 1.2. The new ones, also, no longer support the OTR plugin - The plugin won't work with Gajim >= 1.0 as it was not ported to python3. There is no port planned.
. There are clients out there (e.g mcabber) that do not support OMEMO but do OTR, and this prevents encrypted communication with them. New Gajim is still okay for privacy usage, since it can still disable all the data leaks and supports OMEMO properly. But if the older version is superior, why bother? Gajim does leak data by default. To mitigate Gajim, go to Edit -> Preferences -> Advanced, and disable Allow client / OS information to be sent
as well as Allow local system information to be sent
(you can set it to connect through TOR in the same tab; this option is actually built-in). Gajim retardedly regenerates the leaks upon the creation of every new account, so you have to disable them separately! If you change gajim.$rand to an empty value, you can hide the client name from most clients - but Psi+ and Gajim with special plugins will still expose you. Another bit of mitigation you might want to do is changing the default Google search. For that, go to Preferences -> Advanced -> Advanced Configuration Editor and find the preference search_engine. Insert there your favorite SearX instance. BTW, this is only used when you right click on a selection and choose the Web Search for it option.
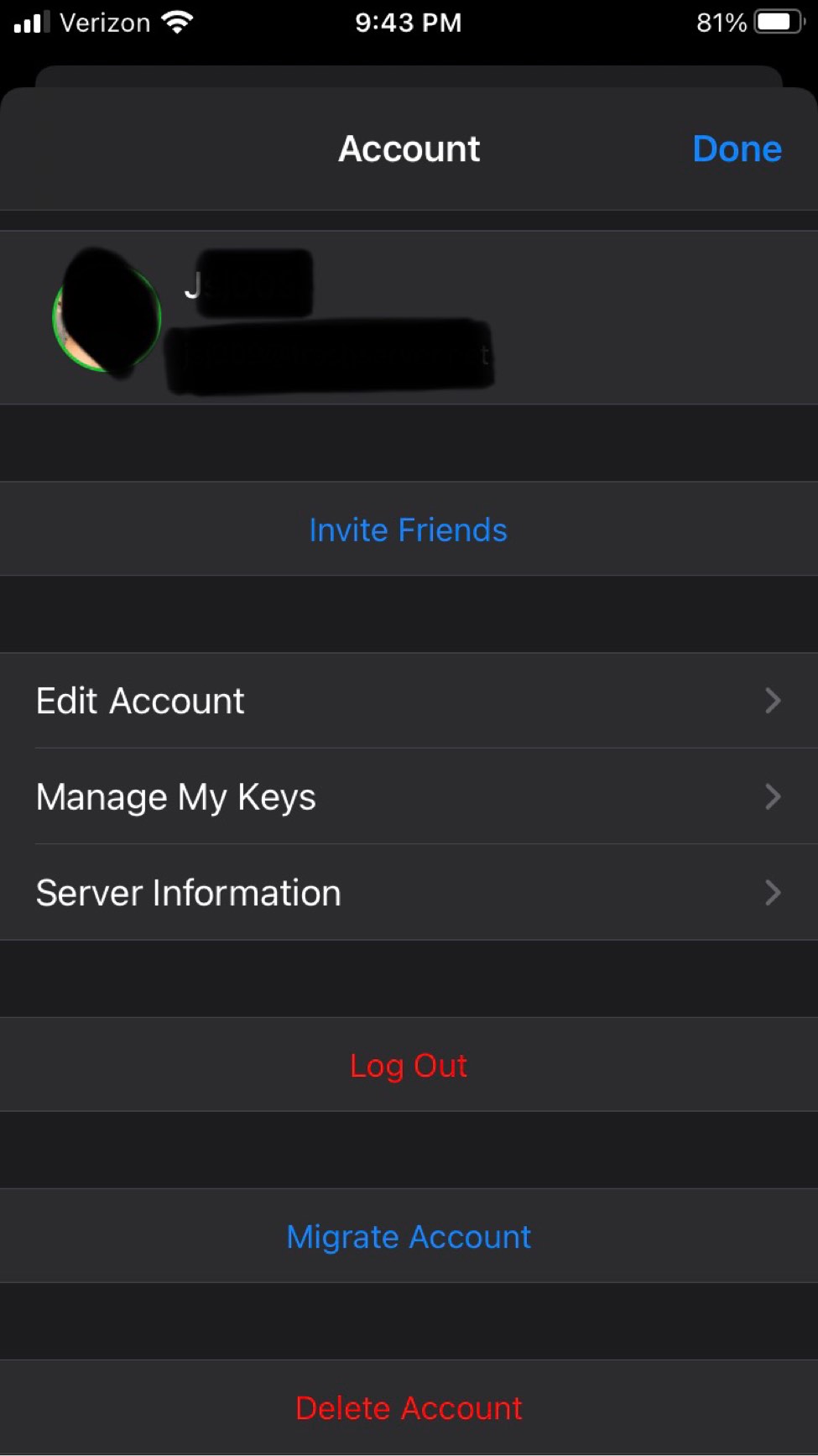
An open source and fully available on GitHub for the IOS App. Unfortunately it's designed specifically and only for IOS mobile devices which are inherently insecure due to the need for Apple's store, and their proprietary data collection methods that cannot be mitigated. In addition to a myriad of privacy risk with using wifi and cellular data plans, Apple's proprietary exclusivity to everything really. Compared to the Android clients, ChatSecure does not reveal its version, timezone, or system information - only the client name in the resource header; this makes it one of the best in terms of data leaks. Notable features that give it some grace:
ChatSecure supports OTR. Not auto-joining group chats or auto accepting OMEMO keys. Has the ability to OMEMO group chats on a per chat basis. ChatSecure also lets users reject or save new OMEMO keys. If you and a friend have not chatted for a while a default message appears and encourages you to verify who you are messaging. Users can also enable auto chat delete when disconnecting and manage downloaded media. Also configuration options for pinned certificates to manage saved SSL Certs. It grants users to add multiple accounts and edit their server information too. It appears to work cross client well too with users using older versions and current production versions. Ironically it lacks the basic copy and paste ability (big frustration with other languages). It is easy for anyone but lacks many features that are necessary for the goal of XMPP/OMEMO, such as MUC whispers.
Written by an anonymous author, who also provided these screenshots:
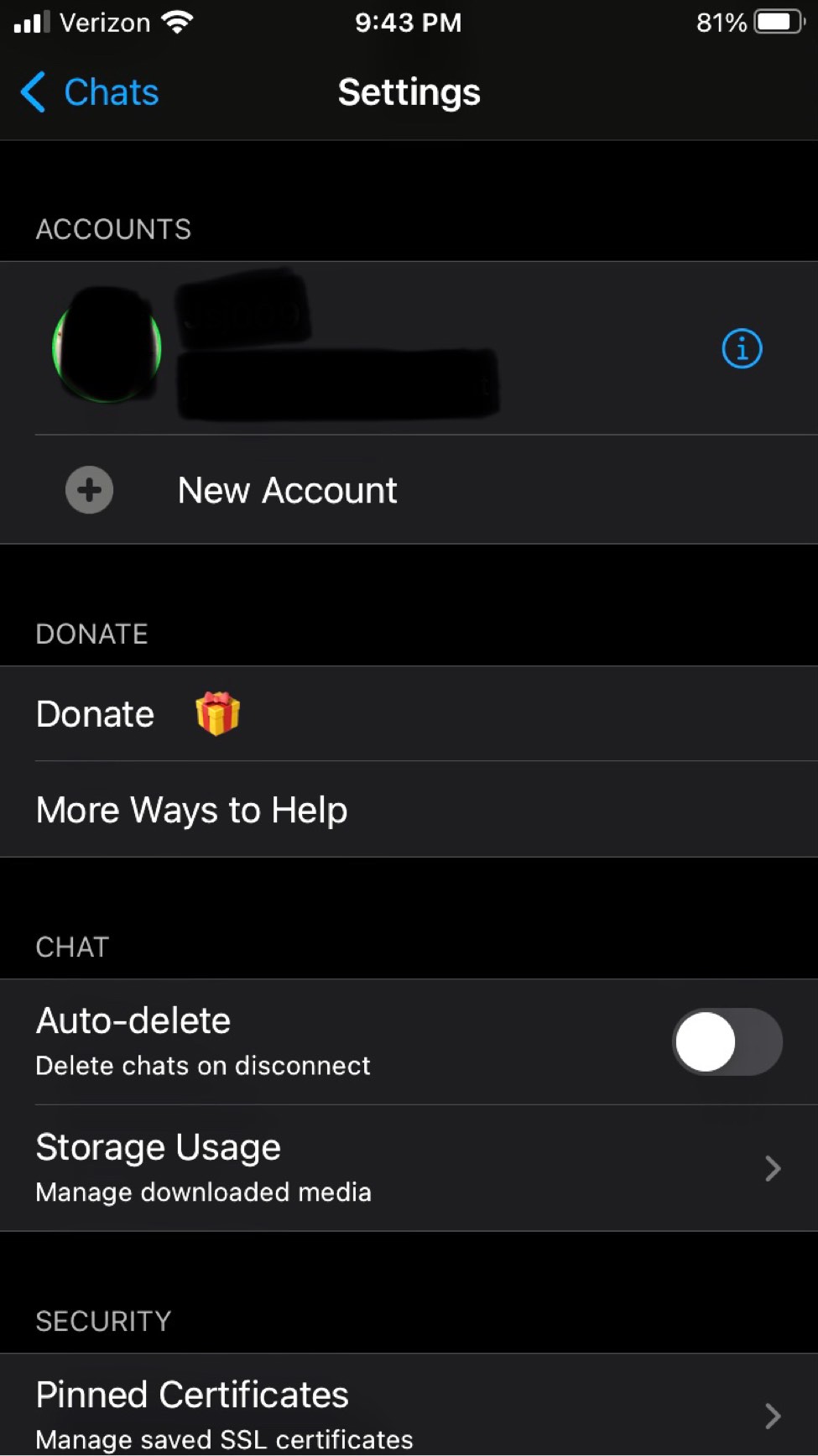
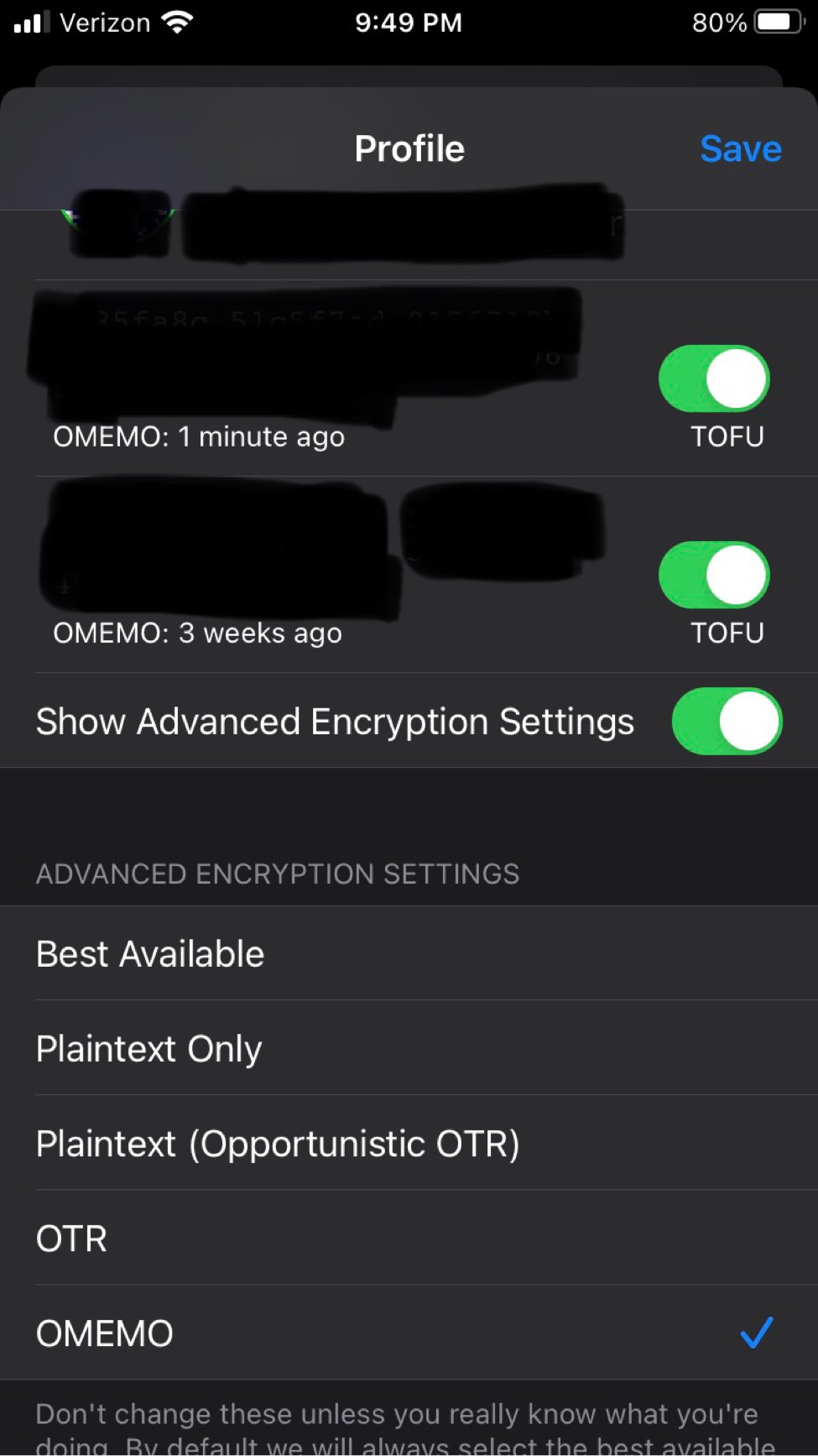
Psi+ is the only client that is able to hide its identity - all other clients can be exposed by Psi+ and Gajim even after attempted mitigations. If you care about client concealement, then you have to use Psi+. Also, when I refer to the resource header, that can only be seen by MUC admins. The most important leak is the timezone, and it can be mitigated in all clients except Pidgin - so don't use it. All Android clients leak timezone unless used through TOR - they also reveal their versions. Profanity can hide everything except its name and version. ChatSecure leaks only the client name, but requires an iPhone to use it. Dino and Gajim (after mitigation) leak only the client name. I did not review any clients that don't support OMEMO, as that is the encryption that is shilled today. Even though OTR is a good replacement, and isn't weaker in any relevant way - I can't justify recommending clients that don't support OMEMO, since they won't be able to have encrypted communication with popular clients that have now dropped OTR (e.g nuGajim). All clients can leak your country through your status messages, if they are in any other language than English. So, use English as your system language or turn off the messages. XMPP servers will always store your roster - the only way to avoid this is to not add anyone to the roster. But then, encryption doesn't work - this is a "flaw" of the protocol.
| Client / Feature | Psi+ | Pidgin | Conversations | Dino | Profanity | Gajim | ChatSecure |
| OMEMO | Yes | Partial | Yes | Yes | Partial | Yes | Yes |
| OTR | Yes | Yes | No | No | Yes | Yes (old versions) | Yes |
| PGP | Yes | 3rd party, didn't test | Yes | Yes | Yes | Yes | No |
| Mitigations for version | Yes | No | No | Yes | No | Yes | Yes |
| Mitigations for timezone | Yes | No | External (TOR) | Yes | Yes | Yes | Yes |
| Mitigations for OS | Yes | Yes | No | Yes | Yes | Yes | Yes |
| Mitigations for client name | Yes | No | No | No | No | Partial | Partial |