Contact me for feedback or questions! I reply to everyone.
People these days worry more and more often about escaping what I will call "The Botnet" in this article - just a "meme" way of describing mass surveillance. Websites have been created describing spyware and alternatives to it. Replacements for social services, instant messaging, VoIP, etc. already exist. You can use anonymizers like the TOR network or a VPN to hide from your ISP. There are ways to privately share files and host websites as well. But are all those effective - and more importantly - is this the core of the botnet - or maybe we're going after this entirely the wrong way?
The TOR network allegedly allows you to browse the Internet anonymously. It works like 3 proxies connected together except encrypted, so a "proxy" (called the TOR node) cannot see the contents of the previous, only the destination. However, the last node does see unencrypted traffic - so we hit a roadblock already before we started. The first node also sees your IP, but not the contents of your request.
What are some other problems with TOR? Well, a lot of websites simply block it, or otherwise try to make its usage inconvenient. Since the list of exit nodes is public, any website owner can easily do it. So you might be planning to "anonymize your browsing", but then realize it's simply unsuitable for everyday usage. Even more so if you intend to actually interact with the websites you're visiting - forums, imageboards, markets, file download websites, etc. all famously hate TOR. If push comes to shove, ISPs could very easily block all TOR traffic as well - in fact this has already happened in Venezuela for example - https://www.accessnow.org/venezuela-blocks-tor/ (archive).
What about the so-called hidden services - exclusive to the TOR network? Well, most of them are defunct and it's hard to find one that actually works - and if you do, mostly you just see some scraps. In my country, I was only able to find ONE onion forum that I could actually connect to, and it didn't have very much activity. Their servers are also routinely raided (see Freedom Hosting) and their owners jailed.
There are many ways of identifying TOR users anyway - browser fingerprinting, stylometry, or even people sharing their personal data while on TOR. Operation Onymous (archive) was very successful (though kind of overstated by the feds - the amount of seized sites were "only" 27 - here is a list). An already famous case of a guy sending a bomb threat using TOR can be read here: https://www.bestvpn.com/privacy-news/harvard-bomb-threat-student-caught-using-guerrilla-mail-tor/ (archive). They got him because he was the only person using TOR on that particular network at the time. The FBI has even paid a university to deanonymize TOR users (archive), and that's how Silk Road 2.0's owner could be locked up. This is just what we know about - more attacks are surely in use or preparation.
TOR still relies on its encryption, and if that's ever broken - say goodbye to your anonymity, since all the traffic is stored for possible future decryption. Though the TOR network does use Perfect Forward Secrecy, which should ensure the security of the encryption keys (without a direct attack on your device) - cracking the actual ciphers is still a possibility:
However, forward secrecy cannot defend against a successful cryptanalysis of the underlying ciphers being used, since a cryptanalysis consists of finding a way to decrypt an encrypted message without the key, and forward secrecy only protects keys, not the ciphers themselves.
Quantum computing makes this likely, too. Another thing that's absolutely required for the security of TOR (that somehow no one is speaking about) are the nine trusted-by-default directory authorities. If a few of those are ever compromised (maybe that's already the case?) all of TOR's advantages go out the window. This issue has been analyzed in depth here.
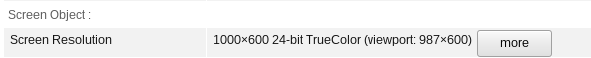
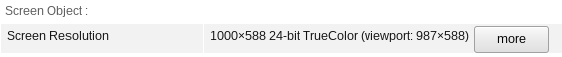
Even the praised TOR Browser is not perfectly safe - for example, just using different buttons in your window manager can expose a different screen resolution (TBB version 8.5.3, newest as of writing). The first theme is Murrine, second - Default XHDPI, if you want to confirm.


Of course, this alone is probably not enough to deanonymize you - but many more issues surely exist, waiting to be discovered. Put a few together and you might just find yourself exposed. Conclusion? TOR is not the panacea. Does that mean you shouldn't use it? No, of course. Use anything that's available to improve your privacy and anonymity - just realize it's not a magic spell, and does not strike at the core of the botnet.
These are proxies that route ALL traffic (not just HTTP) through their servers. There are lots of them claiming to be 'no log', but it is easy to find examples where people got ratted out by these, like https://www.wipeyourdata.com/other-data-erasing/no-logs-earthvpn-user-arrested-after-police-finds-logs/ (archive). Even assuming the 'no log' policy is true, the government could still possibly legally force the provider to track someone (at least in certain countries where that's allowed). If that's not an option, there's always the old raid them and steal the servers (archive) tactic. Of course, VPN traffic is also easily blocked at the ISP or website level.
Simply suffers from lack of usage - so if you want to actually reach anyone, it's Facebook, Skype, etc. Much of the commonly recommended "secure and private" IM software has various issues (Signal and Telegram require a phone number; Keybase has had a security audit which found many issues; Matrix protocol has just had a security issue found (archive)). TOR-based messengers rely on the security of the TOR network, which was analyzed above. Server-based ones, on the other hand, rely on the security of servers controlled by people you don't know. And as usual, it's all going through the enemy's networks.
All regular hosting / file sharing providers have huge lists of what's allowed and what isn't. Even my current host reserves the right to suspend, block or cancel access to any and all
Services
, if they decide something contradicts their list. And of course, copyright holders can claim something is violating theirs, and you get your shit deleted then. Rom sites have been
getting taken down recently for example. There are also 'good hosts' like autistici.org, but who's to say the government won't eventually take them down if they host too much stuff they don't
like? As long as we're using their networks, nothing is safe. Push comes to shove and they raid the servers. Even Freedom Hosting went down eventually.
Alternatives to Windows are available, but you will come across Microsoft's system sooner or later - whether at a relative's house, school, or somewhere else. Not that Linux is all that great either in the botnet department, especially when you consider how it's still controlled by big corpos.
To derive benefit from the Internet's most common services (like Facebook, Twitter, IM, website hosting), you have to deal with their terrible terms of service and privacy policies. Not only that, but any packet you send or receive is physically going through networks that you don't control. ISPs can watch, modify and block them any way they want - and they are subject to government whims as well. Encryption is at best a temporary non-solution, as explained in the TOR section (they could block all encrypted messages easily for example - by comparing them to known languages. If it's not found in any known language, the packet is trashed. Blocking HTTPs? What was it - port 443? Boom and done.). Maybe some smart 'hackers' would learn to bypass these blocks, but in the end, we'd be fighting a battle we're sure to lose. Eventually we're going to have to face the fact that...
As said, servers for the services we use are owned mostly by big corporations (or sometimes other strangers), while ISPs and governments own the networks, so the botnet is physical, not technological - and the solution, by extension, must be as well. This might be hard to see in internet surveillance (which is not even the worst botnet) - but easy in something such as CCTV. They come in, mount the cameras, and boom! You're being watched. You're now their property - which they literally admit to. No really - for 30 days (or some other amount), they can do whatever they want with your captured movements. And the duration is just claimed...Regardless, you're at their mercy now. If they see you engaging in some 'forbidden behavior', they can punish you and they do have a proof you did it. And they can blame you for sins they arbitrarily chose - they certainly aren't asking you if something should be banned or not. Everything in this society is owned by businesses or governments - and so serves their interests, not yours. CCTV is just one example. Drones, killer robots, whatever you can think of - and not necessarily technological. Schools, hospitals, airports (remember the patdowns?) - you have no control of any of these. And that is The Real Botnet. If we want to destroy internet surveillance, we're going to have to take over not only the most popular services' servers (hey, we can have a Facebook that respects the user - no, really!) but also the ISPs - PHYSICALLY - since presumably we won't spy on or censor ourselves...And with that, hopefully we can bury the other botnets as well.
The guy sitting in his apartment wearing a hoodie, running a fully libre ThinkPad, unbreakable Qubes OS, TOR for all connections, carefully avoiding all stylometry and sharing any personal data at all, encrypting his stuff with a one time pad three times, and worrying whether some botnet hasn't slipped in anyway. He has no phone or only uses "burner phones" and pays with bitcoins. And then...he finally has to come out of his house, and has his face recorded by a CCTV camera a hundred times. This guy has to be respected for his dedication, but he is useless for a revolution. You cannot combat The Botnet using tech only.
It is inevitable. And everytime it follows the same script - some country or ISP blocks TOR or VPNs, or torrent sites get taken down, or Facebook / Twitter / YouTube implement yet another way of censorship, or any of the myriad of other issues you can think of. People then freak out and scramble for more technological solutions that are only band-aids. Then, if they find one, they continue their comfortable life while the cuffs get tighter. I mean, can you imagine that, in 20 years, you will be able to use the Internet as freely as today? Impossible - they will keep cracking down on everything until the 'solutions' are too tough or not even viable anymore. If we controlled the infrastructure, we could not only delete all logging ISP-wide, but also fix all the problems with FB / YT / other malicious service providers. Of course, you cannot take over just like that - the web of slavery is too deep - if we just barged in, the police, media etc. would get involved, and that would be the end of it. A full-scale revolution is our only option - and we should use the time during which we can fairly freely talk on the internet to plan for it. Then we could fix not only "The Botnet", but most of the other problems of society.
Hiding or moving the problem. The "federated instances" always suffer from lack of activity, unreliability / short-livedness (hey, why aren't we all hosting our own shit? That's right...), and being subject to the whim of an internet stranger instead of a big corpo. Or take torrents. How many seeds does your favorite anime series have? How about something less popular, like video game soundtracks? People also get notices from their ISPs (VPN / TOR is just moving the problem again) if they didn't like their torrenting; some are apparently fined (archive). And of course, torrent sites still get taken down or compromised (archive). Mesh networks? Yeah, like anyone's going to bother. Even if there theoretically was a decentralized solution worth shit, the governments might simply decide to kill off the whole Internet once they can't control people through it. Edit: or install backdoors in the encryption algorithms or any one of the devices that are used for the meshnet. Again, our enemies have bigger resources / influence than us. Therefore, even decentralization would be temporary in the end - we will need their infrastructure eventually. In that case, we could also take control of something like YouTube or MEGA and keep their popularity and all the content, but change design / policies / TOS, so that users are guaranteed basic respect, privacy and freedom.
If I didn't make my point clear enough earlier, well, I will now. Everything goes back to the physical! We can't keep pretending that putting digital bandages over physical wounds works. The problem is inside the routers, the processors, the datacenters, the wires. The capitalist system that benefits from collecting data. And the legal system that allows and justifies abuses. We need our own factories, our own cities - that are designed with privacy and respect in mind.